Category:Cryptographic algorithms
Jump to navigation
Jump to search
process of encoding information, which is conversion of the original representation of the information, known as plaintext, into an alternative form known as ciphertext | |||||
| Upload media | |||||
| Instance of |
| ||||
|---|---|---|---|---|---|
| Subclass of |
| ||||
| Part of | |||||
| Facet of |
| ||||
| Has use |
| ||||
| |||||
Subcategories
This category has the following 7 subcategories, out of 7 total.
Media in category "Cryptographic algorithms"
The following 62 files are in this category, out of 62 total.
-
5D3L9633 (13189960294).jpg 5,760 × 3,840; 6.19 MB
-
Advantage of IND-CPA Guess Game.svg 267 × 41; 31 KB
-
Aks comparison log.jpg 689 × 379; 157 KB
-
Asymmetric signature algorithms.svg 248 × 125; 26 KB
-
Back ward.png 819 × 646; 30 KB
-
BerlekampMasseyAlgorithm.png 1,776 × 3,223; 44 KB
-
BerlekampMasseyExample01.png 269 × 80; 430 bytes
-
Carré de Polybe avec chiffres et symboles.png 384 × 347; 10 KB
-
Carré de Polybe avec chiffres.png 201 × 205; 6 KB
-
Carré de Polybe Wikipédia.png 171 × 175; 4 KB
-
Carré de Polybe.png 170 × 177; 4 KB
-
Cascade MAC algorithm.svg 406 × 295; 39 KB
-
Cast-256.png 193 × 345; 39 KB
-
Codifica wep.jpg 845 × 350; 22 KB
-
Cryptiom core.png 962 × 722; 153 KB
-
Cryptographic Hash Function.svg 740 × 536; 15 KB
-
CubeHash FlowChart.svg 1,098 × 1,453; 8 KB
-
Decryption.svg 136 × 115; 32 KB
-
Digital signature attacker.svg 173 × 292; 41 KB
-
Dvbcsa block encrypt.svg 1,140 × 790; 34 KB
-
Dvbcsa stream.svg 2,420 × 1,320; 115 KB
-
E-function.png 930 × 682; 142 KB
-
Encryption.svg 136 × 115; 31 KB
-
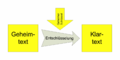
Entschlüsselung (symmetrisches und asymmetrisches Kryptosystem).png 1,400 × 700; 16 KB
-
Forward layer.png 858 × 722; 130 KB
-
GOST-hash-calculation.gif 810 × 112; 2 KB
-
GOST-hash-calculation.svg 810 × 112; 14 KB
-
GOST-psi-function.gif 325 × 196; 3 KB
-
GOST-psi-function.svg 336 × 196; 10 KB
-
GOST-R-34.11-94-shuffle-transformation.gif 518 × 49; 1,007 bytes
-
GOST-R-34.11-94-shuffle-transformation.svg 518 × 49; 12 KB
-
GOST-step-hash-function.gif 184 × 60; 540 bytes
-
GOST-step-hash-function.svg 164 × 60; 6 KB
-
Hash function el.svg 520 × 352; 88 KB
-
Hasq hash chains.png 487 × 377; 26 KB
-
HMACFig2.jpg 684 × 712; 85 KB
-
Homophone Verschluesselung.jpg 858 × 725; 115 KB
-
IND-CPA Guess Cryptographic Game.svg 175 × 175; 61 KB
-
JacobianQuartic.svg 600 × 500; 20 KB
-
Kura 2.jpg 996 × 828; 144 KB
-
Layer up.png 919 × 682; 176 KB
-
Le chiffrement, maintenant.pdf 1,239 × 1,754, 32 pages; 567 KB
-
LEA enc round function.png 1,228 × 694; 36 KB
-
LFSR-F4.GIF 500 × 300; 13 KB
-
MAC algorithms.svg 248 × 182; 20 KB
-
MAC attacker.svg 173 × 292; 34 KB
-
Offsystem.mainline.logo1.png 450 × 300; 59 KB
-
Open TDF Icon.png 98 × 129; 14 KB
-
Permutation finale.svg 1,301 × 707; 241 KB
-
Phelix InfoBox Diagram.png 762 × 246; 8 KB
-
Pohlig-Hellman-Diagram.svg 234 × 142; 40 KB
-
Randu.png 1,280 × 705; 18 KB
-
Randu2.png 239 × 287; 6 KB
-
Ring-signature.svg 259 × 180; 46 KB
-
Rsaalternatives.jpg 780 × 338; 49 KB
-
Sha-family.svg 403 × 507; 27 KB
-
Signature attacker reduction.svg 228 × 289; 70 KB
-
Structure layer.png 962 × 722; 183 KB
-
Tripling oriented.svg 600 × 500; 21 KB
-
Verschlüsselung.ogg 11 min 6 s; 7.48 MB
-
Протокол Т-12.jpg 1,024 × 651; 122 KB
-
クイズ (13189970174).jpg 5,760 × 3,840; 7.51 MB